How To Configure Sftp With Chroot On CentOS 7
Sftp (SSH or Secure file transfer protocol, Instead of using vsftpd we can use sftp, Sftp is the only secure way while comparing to vsftpd. Sftp performs all operations over an encrypted ssh Connection. It has the features of using ssh public key authentication and more as like ssh. If a user only allowed to access his files without ssh shell access we can create a chroot environment for those user’s. While chroot enabled user’s will be jailed into there own home directory.
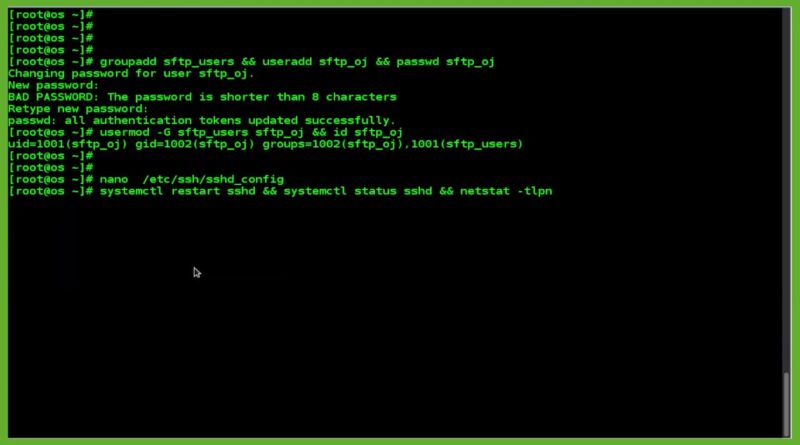
groupadd sftp_users && useradd sftp_oj && passwd sftp_oj
usermod -G sftp_users sftp_oj && id sftp_oj
nano /etc/ssh/sshd_config
#Subsystem sftp /usr/libexec/openssh/sftp-server
Subsystem sftp internal-sftp
Match Group sftp_users
X11Forwarding no
AllowTcpForwarding no
ChrootDirectory /home
ForceCommand internal-sftp
systemctl restart sshd && systemctl status sshd && netstat -tlpn
firewall-cmd –add-service=ssh –permanent && firewall-cmd –reload
setsebool -P ssh_chroot_rw_homedirs on
sftp sftp_oj@192.168.72.153
ssh sftp_oj@192.168.72.153 # Denyed Normally
======================================================
centos 7