Fix Remote Desktop connection issues & errors on Windows 10
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft which provides a user with a graphical interface to connect to another computer over a network connection. The user employs RDP client software for this purpose, while the other computer must run RDP server software. In this post, we will explore how to troubleshoot general Remote Desktop connection issues on Windows 10.

Fix Remote Desktop connection issues
Try the outlined troubleshooting steps below when a Remote Desktop client can’t connect to a remote desktop but doesn’t provide messages or other symptoms that would help identify the cause.
1] Check the status of the RDP protocol on a local computer
You’ll need to enable Remote Desktop to check and change the status of the RDP protocol on a local computer. You can also enable Remote Desktop using Command Prompt or PowerShell.
2] Check the status of the RDP protocol on a remote computer
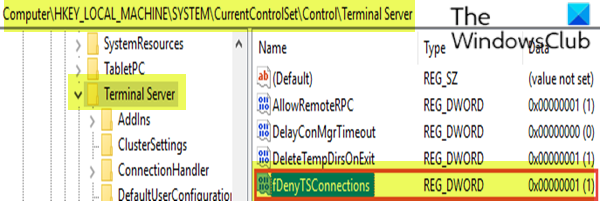
To check and change the status of the RDP protocol on a remote computer, use a network registry connection.
Since this is a registry operation, it is recommended that you back up the registry or create a system restore point as necessary precautionary measures. Once done, you can proceed as follows:
- Press Windows key + R to invoke the Run dialog.
- In the Run dialog box, type
regeditand hit Enter to open Registry Editor. - In the Registry Editor, select File, then select Connect Network Registry.
- In the Select Computer dialog box, enter the name of the remote computer.
- Select Check Names.
- Select OK.
- Next, navigate or jump to the registry key path below:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal Server
- At the location, on the right pane, double-click the fDenyTSConnections key to edit its properties.
- To enable RDP, set the Value data of fDenyTSConnections from 1 to 0.
The value of 0 indicates RDP is enabled, while the value of 1 indicates RDP is disabled.
3] Check whether a Group Policy Object (GPO) is blocking RDP on a local computer
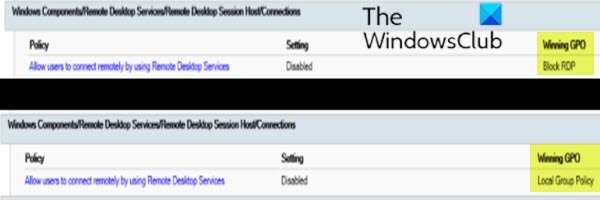
A GPO may be overriding the computer-level settings, if you can’t turn on RDP in the user interface or the value of fDenyTSConnections reverts to 1 after you’ve changed it
To check the group policy configuration on a local computer, do the following:
- Press Windows key + R to invoke the Run dialog.
- In the Run dialog box, type
cmdand then press CTRL + SHIFT + ENTER to open Command Prompt in admin/elevated mode. - In the command prompt window, type the command below and hit Enter.
gpresult /H c:gpresult.html
- Once the command executes, open gpresult.html.
- In Computer ConfigurationAdministrative TemplatesWindows ComponentsRemote Desktop ServicesRemote Desktop Session HostConnections, find the Allow users to connect remotely by using Remote Desktop Services policy.
If the setting for this policy is Enabled, Group Policy is not blocking RDP connections. If the setting for this policy is Disabled, check Winning GPO. This is the GPO that is blocking RDP connections.
4] Check whether a GPO is blocking RDP on a remote computer
To check the Group Policy configuration on a remote computer, run the command below in elevated CMD prompt:
gpresult /S <computer name> /H c:gpresult-<computer name>.html
The file that this command produces (gpresult-<computer name>.html) uses the same information format as the local computer version (gpresult.html) uses.
5] Modify a blocking GPO
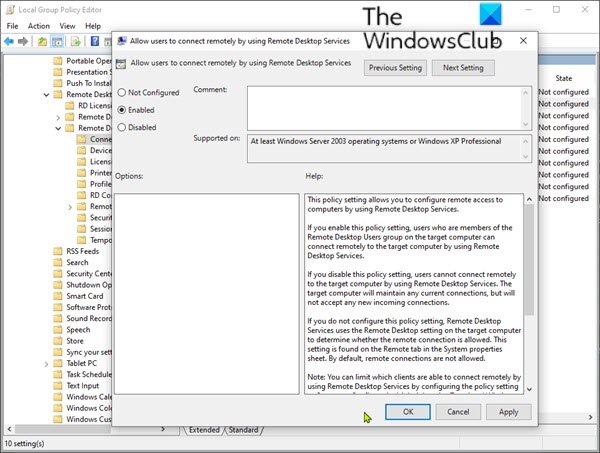
You can modify these settings in the Group Policy Object Editor (GPE) and Group Policy Management Console (GPMC).
To modify the blocking policy, use one of the following methods:
Using GPE, do the following:
- Press Windows key + R to invoke the Run dialog.
- In the Run dialog box type
gpedit.mscand press Enter to open Group Policy Editor. - Inside the Local Group Policy Editor, use the left pane to navigate to the path below:
Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections
- At the location, on the right pane, double click the Allow users to connect remotely by using Remote Desktop Services.to edit its properties.
- Set the policy to either Enabled or Not configured.
- Click Apply > OK and exit.
- On the affected computers, open a command prompt window as an administrator, and run the command below:
gpupdate /force
Using GPMC, navigate to the organizational unit (OU) in which the blocking policy is applied to the affected computers and delete the policy from the OU.
6] Check the status of the RDP services
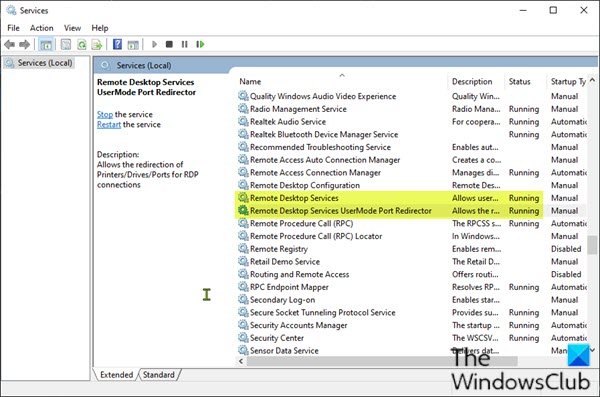
On both the local (client) computer and the remote (target) computer, the following services should be running:
- Remote Desktop Services (TermService)
- Remote Desktop Services UserMode Port Redirector (UmRdpService)
On either computer, if one or both services are not running, start them.
Do the following:
- Press Windows key + R to invoke the Run dialog.
- In the Run dialog box, type
services.mscand hit Enter to open Services. - In the Services window, scroll and locate both aforementioned service.
- Double-click on the entry to edit its properties.
- In the properties window, click the Start button.
- Click OK.
You can also use PowerShell to manage the services locally or remotely (if the remote computer is configured to accept remote PowerShell cmdlets).
7] Check the status of the RDP listener
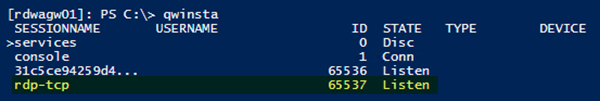
This procedure uses PowerShell because the same cmdlets work both locally and remotely. For a local computer, you can also use a command prompt that has administrative permissions.
To connect to a remote computer, do the following:
Enter-PSSession -ComputerName <computer name>
If the list includes rdp-tcp with a status of Listen, as shown in the image above, the RDP listener is working. Jump to the Troubleshooting step 10] below. Otherwise, you’ll need to export the RDP listener configuration from a working computer.
Do the following:
- Sign in to a computer that has the same operating system version as the affected computer has, and access that computer’s registry.
- Navigate or jump to the following registry entry:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal ServerWinStationsRDP-Tcp
- Export the entry to a .reg file.
- Copy the exported .reg file to the affected computer.
- To import the RDP listener configuration, open a PowerShell window that has administrative permissions on the affected computer (or open the PowerShell window and connect to the affected computer remotely).
To back up the existing registry entry, enter the following cmdlet:
cmd /c 'reg export "HKLMSYSTEMCurrentControlSetControlTerminal ServerWinStationsRDP-tcp" C:Rdp-tcp-backup.reg'
To remove the existing registry entry, enter the following cmdlets:
Remove-Item -path 'HKLM:SYSTEMCurrentControlSetControlTerminal ServerWinStationsRDP-tcp' -Recurse -Force
To import the new registry entry and then restart the service, run the cmdlets below. Replace the <filename> placeholder with the name of the exported .reg file.
cmd /c 'regedit /s c:<filename>.reg' Restart-Service TermService -Force
Once done executing the cmdlets, you can test the configuration by trying the remote desktop connection again. If you still can’t connect, restart the affected computer.
If you still can’t connect, proceed with the next troubleshooting step which is to check the status of the RDP self-signed certificate.
8] Check the status of the RDP self-signed certificate
If you still can’t connect, do the following:
- Press the Windows key + R to invoke the Run dialog.
- In the Run dialog box, type
mmcand hit Enter to open Microsoft Management Console. - Click the File menu.
- Select Add/Remove Snap-in.
- Select Certificates from the list of snap-ins.
- Click Add.
- When you are prompted to select the certificate store to manage, select Computer account.
- Click Next.
- Select the affected computer.
- Click the Finish button.
- Click OK.
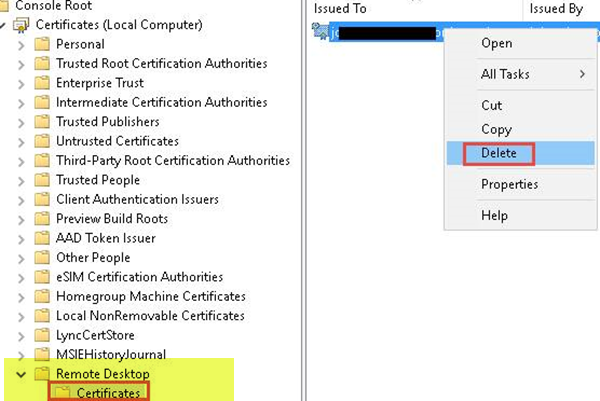
- Now, in the Certificates folder under Remote Desktop, delete the RDP self-signed certificate.
- On the affected computer, restart the Remote Desktop Services service.
- Refresh the Certificates snap-in.
- If the RDP self-signed certificate has not been recreated, check the permissions of the MachineKeys folder.
9] Check the permissions of the MachineKeys folder
On the affected computer, do the following:
C:ProgramDataMicrosoftCryptoRSA
- At the location, right-click MachineKeys, select Properties, select Security, and then select Advanced.
Make sure that the following permissions are configured:
- BuiltinAdministrators: Full control
- Everyone: Read, Write
10] Check the RDP listener port
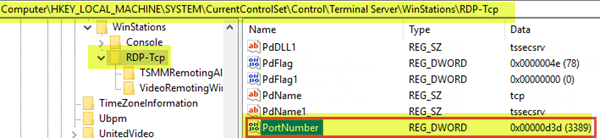
On both the local (client) computer and the remote (target) computer, the RDP listener should be listening on port 3389. No other applications should be using this port.
To check or change the RDP port, use the Registry Editor. As a precautionary measure back up the registry or create a system restore point, then continue as follows:
- Open Registry Editor, select File, then select Connect Network Registry.
- In the Select Computer dialog box, enter the name of the remote computer.
- Select Check Names.
- Select OK.
- Next, navigate or jump to the registry key path below:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal ServerWinStationsRDP-Tcp
- At the location, on the right pane, double-click the PortNumber entry to edit its properties.
- In the properties window, if the Value data field has a value other than 3389, change it to 3389.
- Click OK to save changes.
- Restart the Remote Desktop Services service.
11] Check that another application isn’t using the same port
Do the following:
- Open a PowerShell in elevated mode.
- To connect to a remote computer, run the command below:
Enter-PSSession -ComputerName <computer name>
Next, run the following command:
cmd /c 'netstat -ano | find "3389"'
- Look for an entry for TCP port 3389 (or the assigned RDP port) with a status of Listening.
Note: The process identifier (PID) for the process or service using that port appears under the PID column.
- To determine which application is using port 3389 (or the assigned RDP port), enter the following command:
cmd /c 'tasklist /svc | find "<pid listening on 3389>"'
- Look for an entry for the PID number that is associated with the port (from the
netstatoutput). The services or processes that are associated with that PID appear on the right column. - If an application or service other than Remote Desktop Services (TermServ.exe) is using the port, you can resolve the conflict by using one of the following methods:
Configure the other application or service to use a different port (recommended).
Uninstall the other application or service.
Configure RDP to use a different port, and then restart the Remote Desktop Services service (not recommended).
12] Check whether a firewall is blocking the RDP port
You can use the psping tool to test whether you can reach the affected computer by using port 3389.
Do the following:
- Go to a different computer that isn’t affected and download psping.
- Open a command prompt window as an administrator, change to the directory in which you installed psping, and then enter the following command:
psping -accepteula <computer IP>:3389
- Check the output of the psping command for results such as the following:
Connecting to <computer IP>: The remote computer is reachable.
(0% loss): All attempts to connect succeeded.
The remote computer refused the network connection: The remote computer is not reachable.
(100% loss): All attempts to connect failed.
- Run psping on multiple computers to test their ability to connect to the affected computer.
- Note whether the affected computer blocks connections from all other computers, some other computers, or only one other computer.
Additional steps you can take includes;
- Engage your network administrators to verify that the network allows RDP traffic to the affected computer.
- Investigate the configurations of any firewalls between the source computers and the affected computer (including Windows Firewall on the affected computer) to determine whether a firewall is blocking the RDP port.
Hope this post can help you successfully troubleshoot RDP connection issues you might be having!

- Tags: Remote Desktop, Troubleshoot