Configure Remote Access Client Account Lockout in Windows Server
[ad_1]
Businesses that deploy Windows Server to manage computers and other policies are crucial. The nice part about managing servers is that you don’t have to be physically around it. You can always remotely log in to the server from anywhere. That means somebody else can also try to login as well. In this post, we will share how you can configure Remote Access Client Account Lockout in Windows Server using the Registry method.

Configure Remote Access Client Account Lockout
If you are wondering why there is a lockout setup in place, then it is to make sure to keep attackers at bay. Once you design, it will not only make sure to keep attackers who do guesswork but also those who perform a dictionary attack. It can happen to a valid user who doesn’t remember the exact password. The lockout makes sure that the user will not be able to try to attack for some period of time, making the overalls security better.
However, it also means that it can lock out legitimate users, which can annoy. In this post, we will also show how you can manually unlock a remote access client.
Depending on what you are using for authentication, configure the registry settings accordingly. If you are using Microsoft Windows Authentication, then configure the registry on Remote Access Server. But if you are using RADIUS for RAS, then configure it on Internet Authentication Server or IAS.
Here is the list of things we will configure:
- Number of failed attempts before lockout
- The time after which the lockout counter is reset
Make sure to take a backup of the registry before making any changes.
Enable Remote Access Client Account Lockout
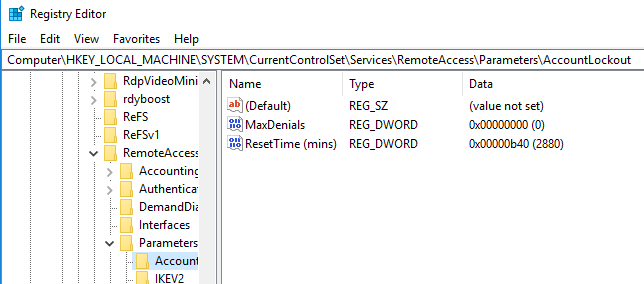
Open Registry Editor by typing Regedit in the Run prompt and press the Enter key. Locate and then click the following registry key:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesRemoteAccessParametersAccountLockout
Locate and then double-click the MaxDenials value. Set the value to anything above zero, which will also mean it is the number of failed attempts. So if you set to two, the third attempt will result in a lockout. Click OK to confirm
Next, double-click on the ResetTime (mins) value, which is in hexadecimal. The default value is set for two days, so make sure to put it according to the policy your company follows.
Click OK, and then quit Registry Editor.
Registry Editing to manually unlock a Remote Access Client
Assuming you have a locked account, and you need to unlock because the lockout timeout is pretty long. Every time a user is locked out, an entry is made into it in the format of DomainName:UserName. To remover the lock, you need to delete it.
- Open the Registry Editor and navigate to the following path.
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesRemoteAccessParametersAccountLockout
- Find the Domain Name:User Name value, and then delete the entry.
- Quit Registry Editor and check if the user account is able to login with the right credentials.
That’s about it. Always make sure to backup registry settings before you make any changes.
I hope the post gave you clear insight on how you can configure lockout and also unblock a remote client.



