How Hackers Move Through Networks (with Ligolo)
https://jh.live/vanta || Prove your security compliance with Vanta! Get $1,000 off with my link: https://jh.live/vanta
The Pivoting Lab SnapLabs template: https://jh.live/pivoting
Free Cybersecurity Education and Ethical Hacking
🔥YOUTUBE ALGORITHM ➡ Like, Comment, & Subscribe!
🙏SUPPORT THE CHANNEL ➡ https://jh.live/patreon
🤝 SPONSOR THE CHANNEL ➡ https://jh.live/sponsor
🌎FOLLOW ME EVERYWHERE ➡ https://jh.live/discord ↔ https://jh.live/twitter ↔ https://jh.live/linkedin ↔ https://jh.live/instagram ↔ https://jh.live/tiktok
💥 SEND ME MALWARE ➡ https://jh.live/malware
by John Hammond
linux web server


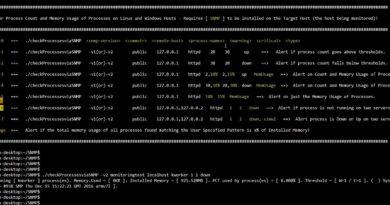

Sorry, I just added the Pivoting Lab SnapLabs template link now: https://jh.live/pivoting
Thanks for watching and all your support! (and psst, check out Vanta! https://jh.live/vanta)
Isn’t the certificate generated on the proxy side ie your kali box that does have internet? And then the TLS certificate can be verified offline by the agent
I’m not a computer expert, Jack Rhysider warped my brain so I listen to videos like this to relax at bedtime
Very cool and thanks for the video!
Feedback: The multiple camera views of the video I am not the biggest fan of at this time. I feel more connected to the content when its the straight on camera angle where you are engaged with the viewers, when it switches seeing you looking in a different direction makes it feel disconnected from the content. If you plan on keeping the multiple angles personally I would like to see you engage the camera that is active. Appreciate all the new content you are producing! That is my .02.
Its easier to social engineer today directly to internal network via employee weakness (especially new people to country)
About spinning up sanboxies. Have you tried vagrant? It's kinda awesome tool to spin up multiple vms with custom networking and different images and it supports ssh and winrpc connectivity and Ansible playbooks for software provision as well
does this mean you will be able to access the subnet of the companies assuming they are using active directory
I can tell you're reading from a screen or something.
Awesome mate Thanks
Explaining what Kali is and what is a "cross-platform" software while presenting a network pivoting tool for advanced pentesters is killing me
Thank you so much John for sharing, all that super useful knowledge with us. I realy enjoying watching your videos. 👍
💥EXCELLENT VIDEO – GREAT SKILLS SHARING – MUST WATCH – THANK YOU 💥
Ligolo ftw! I used a lot for htb pro labs
Sir , after completing bca course then what course should we take to fully completed cybersecurity or Ethical hacking
Cool Video 📼
How I wish these tools were not honeypots developed by Blue Team or the Government 😅 😡🙂😄
Just stick with the tradition 🤗 you what I mean.
Cool video Thanks 🎉
I like this but the name ligolo is kinda weird 💀… ngl
Can you make a video on protecting against this or simply show how to setup a detector for it? That would be sick. I had to subscribe after watching this demo, very well done!
In my experience, servers in a DMZ don't have a second interface on an internal subnet- that defeats the purpose of the DMZ.
Just did this pivoting and hacked my local police department and they loved it! They even offered me a free room with free toilet and nice orange clothes! Life is good!
Occupy The Web always gives Bombal the "best cyber security youtube channel" tag every time he's in one of his videos, and I love OTW, he's a great dude, but if you know your ass from your elbow it's clear to see that John Hammond is the king of showing you novel techniques and actionable information that you can add to your toolbox and use. The only reason OTW doesn't say so is because John doesn't need to have other people come on and do his videos for him every week because this man knows his shit!
this is super clean content now i love it. Love the examples shown
Where was this program when i took eCPPT? great video!!
I tried using the autocert but it seems to have an issue. "yamux: Failed to write header: acme/autocert: missing server name
ERRO[0151] could not register agent, error: session shutdown". For the purposes of taking exams and stuff though, this is super awesome, don't need real certs.
Oh, don’t advocate for “real” certs. That’s evidence! Self-signed cert is perfect for this application.
I have no idea WTF just happened…
I don't give a shit tbh
So how do you protect against this attack?
thats not informative video, its only advertisement. Doesn't show any how-to-use technique and etc, also editing is pretty bad of video switching screens so fast is bad technique
Started using this tool yesterday…
Hopefully, I'll get to understand it here
I like this new version videos
this tool would make the job a lot easier thank you for the demo man keep up the good work much love from Saudia Arabia <3
Thanks
John Hammond more Tut like this plz
"ligolo-ng can work on any machine. Linux, Windows and Mac"
Imagine a company using Macs as their servers 💀
What is the CN of the let’s encrypt certificate? Perhaps you could easily traverse ligolo certificates via the certificate transparency database…
I love how you've grown into cybersecurity. I'm very rusty and think your videos are helping eliminate that rust.
Can we still use this in network client isolation network ? I mean if the access restricted network withing the same vlan clients ?
im so glad i learned how to use ligolo before doing the CPTS exam. passed on the exam in august on the first attempt <3
Nice Video. But in my opinion it is a little to hectic. The cuts look cool, but they are a bit confusing.