SSH Honeypot in 4 Minutes – Trap Hackers in Your Server
In this video I’ll show you a funny way to protect your SSH server from hackers, script kiddies and Chinese botnets, using Endlessh by Chris Wellons
Endlessh (GitHub): https://github.com/skeeto/endlessh
Support the channel:
Patreon https://patreon.com/WolfgangsChannel
PayPal (one time donation) https://www.paypal.com/donate/?hosted_button_id=S46R487SBMJZ8
Follow me:
Twitter https://twitter.com/notthebeeee
GitHub https://github.com/notthebee
Music:
A.M. Beef – Takama no Hara
Ian Post – Electricity
by Wolfgang’s Channel
linux web server


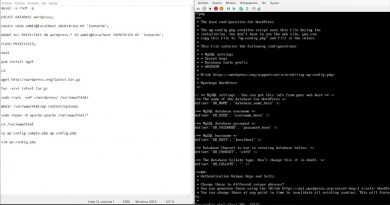

Please note that Endlessh is NOT meant to replace conventional SSH security methods. You should still set up public-key only authentication and 2FA, as well as tools like iptables, fail2ban and CrowdSec
It's also not meant to protect you from nmap port scans or advanced attacks. Endlessh is a fun way to mess with automated SSH scanners, but that's it.
banner are a bit stupid imho it helps detecting fake ssh
This no longer works, just so you know. Not on Ubuntu at least.
Hey what server do you use for a server
If you're using PAM you can delay your real ssh daemon too, edit /etc/pam.d/sshd and add
auth optional pam_faildelay.so delay=10000000
For a 10 second delay, or
auth optional pam_faildelay.so delay=60000000
For a 60 second delay.
Still not the best way to deal with automated SSH scanners, but it should slow them.
For remote access (that is, not whitelisted) access to accounts on my server — or at least those accounts for which such access is permitted — the password and then two different ssh keys are required. So far, it doesn't appear that anyone has ever gotten the password.
My only concern is that there could be some 0 day vulnerability that could bypass those. Unlikely, I think, but I don't know that it can be entirely counted out.
What a great solution! 😀
Thanks!
Do you have any idea how to setup PFSense Firewall with Fail2Ban ?
The freemasons had the white girl pretend to randomly cross my path at church. The goal was for her to see me in a poor humiliating position.
Imagine you perform a reverse denial of service attack when they log in or exploit a vulnerability in their ssh client.
For non script kiddies this video is easy to circumvent. Just put a timeout to get a shell and move on. Log IP and credentials for later manual review.
i was searching this 🙂
Additionally you should created an alternative account to login and forbit ssh access for root
disappointing no longer works on
Is this cmd or powershell? Why i can't do it?
Endlessh is such a good idea, thank you for sharing it!
I do regret changing my ssh port, though, because I now run VPNs on port 22 and run my Forgejo instance on port 2222… It's a total nightmare in terms of compatibility, because I now have a bunch of programs that doesn't recognize my git repo addresses.
My Server Right now
Status for the jail: sshd
|- Filter
| |- Currently failed: 9
| |- Total failed: 9342
| `- File list: /var/log/auth.log
`- Actions
|- Currently banned: 7
|- Total banned: 1482
`- Banned IP list: 201.79.59.222 36.156.112.13 72.167.41.167 138.197.215.196 144.126.204.43 61.177.173.48 41.60.239.160
A large part of the bandwidth consumed by my relatively unused web server, seems to be these failed ssh bots. What's the difference if my server is sending them gibberish, per each attempt. If it takes 20sec to send them garbage, opposed to them attempting every 0.2 seconds, would I be saving bandwidth?
I deployed this on my server the other day (I already had SSH on a different port than default and set up public key login only) and I’ve already had countless bots attempt to SSH in. Some got stuck for over 20 minutes. There’s been bots from Russia, China, Peru, the UK, South Korea, all over the damn place.
Pretty cool knowing that not only am I doing my part to waste these assholes’ time, but I’m also better protecting my server. I’m willing to bet that with a number of these bots, after they get trapped in the tarpit they probably blacklist your server’s IP so they don’t waste their time again.
You look like you would look good with a austrianpainterAdolf mustache
Wow I need this. Just had my Nextcloud server hacked for the 6th time. Getting really tired of losers wasting my time.
Let's do this face to face and see who will walk out alive.
3:42 nothing is fixed you have open port. lets bufferoverflow!
2:00 yes its that easy wrong many time BOOM ur out! i dont get it how can bruteforce any server
ssh-copy-id user@your_server_address
ssh user@your_server_address
is that funny its all build in just send your public key and login
it ask password for user. so what port 22 is open for hacker 😛
if port 22 is closed hacker not come 😛
use reverse ssh so you not have open port 😛