Configure Controlled Folder Access using Group Policy & PowerShell
Controlled folder access is an intrusion-prevention feature available with Microsoft Defender Exploit Guard, which is part of the Microsoft Defender Antivirus. It’s been designed primarily to prevent ransomware from encrypting your data/files, but it also protects files from unwanted changes from other malicious applications. In this post, we will show you how to configure Controlled Folder Access using Group Policy & PowerShell in Windows 10.
This feature is optional on Windows 10 but when enabled, the feature is able to track executable files, scripts, and DLLs, that attempt to make changes to files in the protected folders. If the app or files is malicious or not recognized, the feature will block the attempt in real-time, and you’ll receive a notification of the suspicious activity.
Configure Controlled Folder Access using Group Policy
To configure Controlled Folder Access using Group Policy, you first need to enable this feature. Once done, you can proceed to configure the following:
Add new location for protection via Local Group Policy Editor
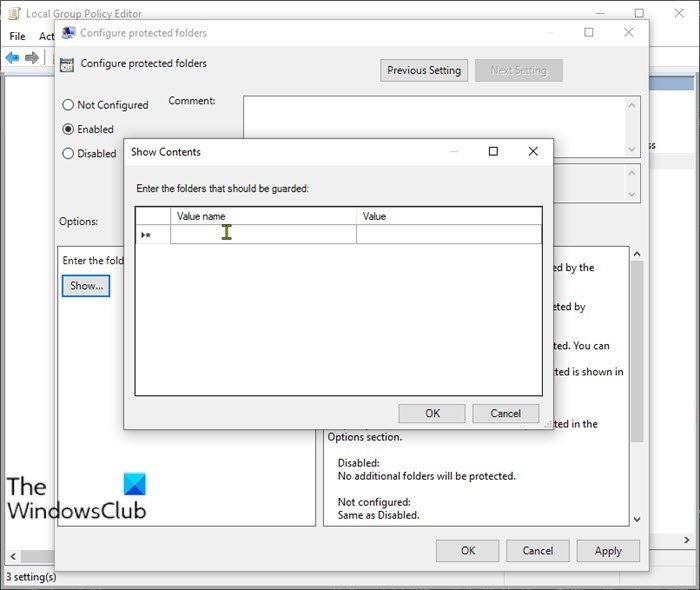
If Controlled folder access is enabled, the basic folders are added by default. If you must protect data located in a different location, then you can use the Configure protected folders policy to add the new folder.
Here’s how:
- Press Windows key + R to invoke the Run dialog
- In the Run dialog box type
gpedit.mscand hit Enter to open Group Policy Editor. - Inside the Local Group Policy Editor, use the left pane to navigate to the path below:
Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Controlled Folder Access
- Double-click the Configure protected folders policy on the right pane to edit its properties.
- Select the Enabled radio button.
- Under the Options section, click the Show button.
- Specify the locations you want to protect by entering the path of the folder (eg;
F:MyData) in the Value name field and adding 0 in the Value field. Repeat this step to add more locations. - Click the OK button.
- Click the Apply button.
- Click the OK button.
The new folder(s) will now be added to the protection list of Controlled folder access. To revert the changes, follow the instructions above, but select the Not Configured or Disabled option.
Whitelist apps in Controlled folder access using Local Group Policy Editor
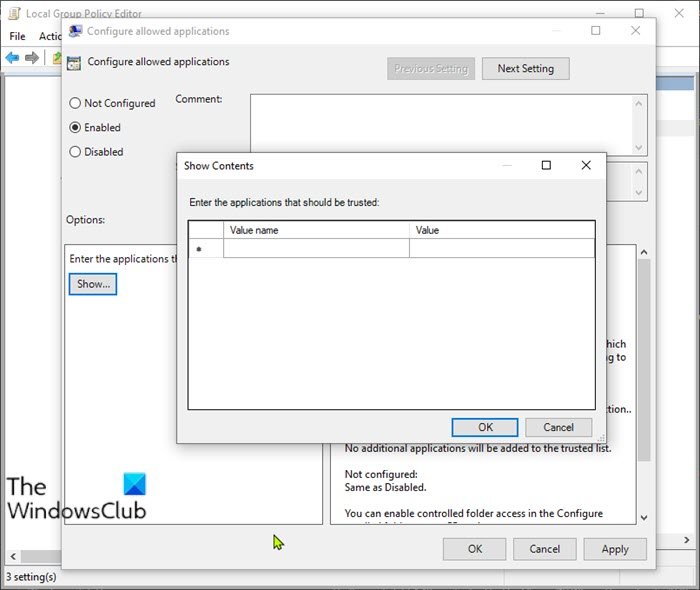
- Open Local Group Policy Editor.
- Inside the Local Group Policy Editor, use the left pane to navigate to the path below:
Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Controlled Folder Access
- Double-click the Configure allowed applications policy on the right pane to edit its properties.
- Select the Enabled radio button.
- Under the Options section, click the Show button.
- Specify the location of the .exe file for the app (eg;
C:Program Files (x86)GoogleChromeApplicationchrome.exe) you want to allow in the Value name field and add 0 in the Value field. Repeat this step to add more locations. - Click the OK button.
- Click the Apply button.
- Click the OK button.
Now, the specified app(s) won’t be blocked when Controlled folder access is turned on, and it’ll be able to make changes to protected files and folders. To revert the changes, follow the instructions above, but select the Not Configured or Disabled option.
For Windows 10 Home users, you can add Local Group Policy Editor feature and then carry out the instructions as provided above or you can do the PowerShell method below.
Configure Controlled Folder Access using PowerShell
To configure Controlled Folder Access using Group Policy, you first need to enable the feature. Once done, you can proceed to configure the following:
Add new location for protection using PowerShell
Add-MpPreference -ControlledFolderAccessProtectedFolders "F:folderpathtoadd"
In the command, substitute the F:folderpathtoadd placeholder with the actual path for the location and executable of the app you want to allow. So for example, your command should look like the following:
Add-MpPreference -ControlledFolderAccessProtectedFolders "F:MyData"
- To remove a folder, type the command below and hit Enter:
Disable-MpPreference -ControlledFolderAccessProtectedFolders "F:folderpathtoremove"
Whitelist apps in Controlled folder access using PowerShell
- Launch PowerShell in admin/elevated mode.
- In the PowerShell console, type in the command below and hit Enter.
Add-MpPreference -ControlledFolderAccessAllowedApplications "F:pathtoappapp.exe"
In the command, substitute the F:pathtoappapp.exe placeholder with the actual path for the location and executable of the app you want to allow. So for example, your command should look like the following:
Add-MpPreference -ControlledFolderAccessAllowedApplications "C:Program Files (x86)GoogleChromeApplicationchrome.exe"
The above command will add Chrome to the list of allowed apps and the app will be allowed to run and make changes to your files when Controlled folder access is enabled.
- To remove an app, type the command below and hit Enter:
Remove-MpPreference -ControlledFolderAccessAllowedApplications "F:pathtoappapp.exe"
That’s it on how to configure Controlled Folder Access using Group Policy & PowerShell in Windows 10!