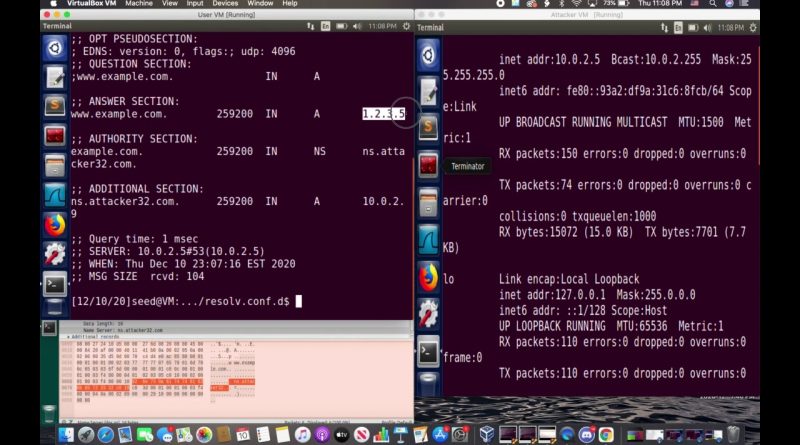
DNS Cache Poisoning Attack Demo
• Used the attacker machine to send DNS cache poisoning responses to the server machine which poisoned the DNS server for the user
• The user machine served as the victim. When the user sends a DNS request to access a web server, “example.com”, it sends the DNS request to the server machine. The attacker’s goal is to spoof DNS responses and send back to the server.
• The user machine will then get the malicious DNS response from the attacker machine
• Use the dig command to find out the IP address of example.com. If the IP address is of the attacker machine, the attack is successful
by CyberCat
linux dns server



What type of os do you use?
can u help me giving code??
please is so important for me…
can u help me giving code or link where find it?
Hello, Hello, what is the software and code used in the video, I hope to provide below the video at the next recording video. thanks
I really like your video dns cache poisoning attack. but i don't know how to write program attack.c. Can you show me the program attack.c or any link to download it. thank you very much.
👍
Wow that was well explained
Great work