Hacking Into a Domain Controller (Windows Server 2016) – ZeroLogon
Hacking Into a Domain Controller (Windows Server 2016):
– Target IP : 192.168.91.139 (Windows Server 2016)
– Attacker’s IP : 192.168.91.134 (Kali Linux)
#Attack_Steps:
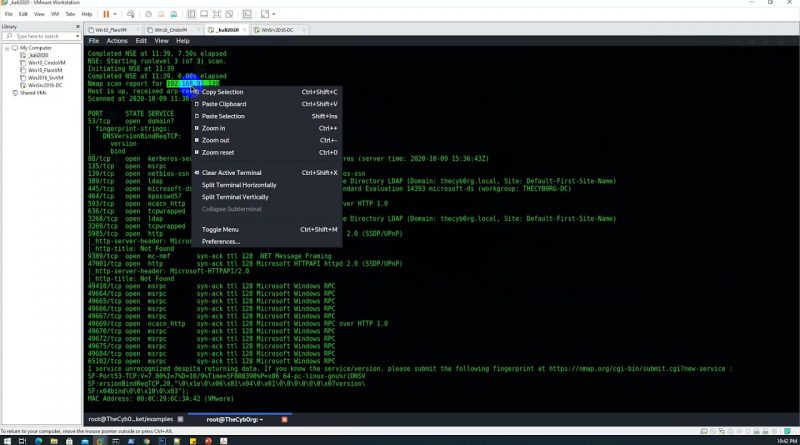
1. Identify target IP address
2. Identify opened ports and obtained associated information from the target
3. Identify if the target is vulnerable to Zerologon Vulnerability (CVE-2020-1472)
4. Reset the domain machine password into empty strings
5. Perform DCsync attack against the target to extract passwords hashes
6. Gain access into the target using Pass-The-Hash technique
As demonstrated, the domain controller (Windows Server 2016) is vulnerable to Zerologon Vulnerability (CVE-2020-1472) which could allow a remote attacker to gain control over the domain controller without user interaction.
#Mitigation:
Check for the necessary actions required recommended by Microsoft.
#Disclaimer:
For demonstration and educational purpose only. The demonstration has been conducted within a controlled lab (#THECyb0rg Lab) environment. — #TheCyb0rg
windows server