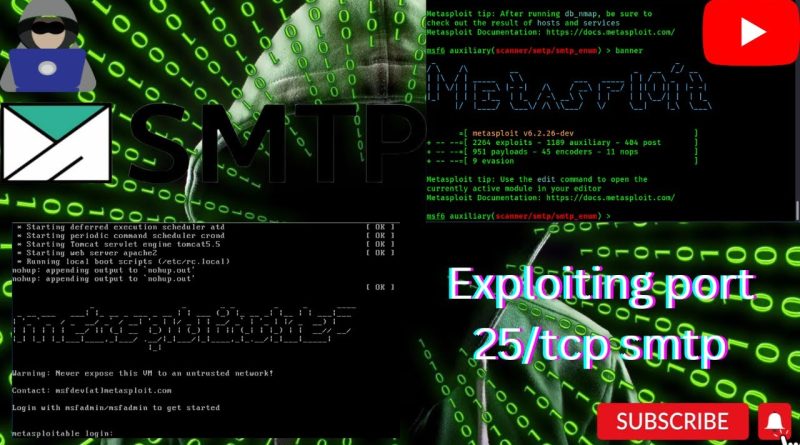
How to Exploit SMTP Port 25: Kali Linux – Metasploitable2 – V-4
How to Exploit Telnet Port 25: Kali Linux – Metasploitable2 – V-4
SMTP, which stands for Simple Mail Transfer Protocol, is an email protocol used for sending email messages from one email account to another via the internet.
so in this video i explain how to exploit SMTP service which runs on port no.25
—————————————————————————————————————————
How to Exploit Telnet Port 23: Kali Linux – Metasploitable2 – V-3: https://youtu.be/aNcqaoAGdzY
How to Exploit SSH Port 22: Kali Linux – Metasploitable2 – V-2: https://youtu.be/8T-iltE45mc
—————————————————————————————————————————
if you have any qution about this video feel free to ask me at Telegram.
Telegram channel: https://t.me/TECH_JOKER
—————————————————————————————————————————
kali linux,how to hack,hacking,kali linux tutorial,how to install kali linux,kali linux install,how to exploit open ports using metasploit,port 25 smtp exploit,exim smtp,exploit smtp,postal email server,about smtp,how to enumarate port25,how to exploit port 25,simple mail transfer protocol (smtp),simple mail transfer protocol,simple mail transfer protocol in hindi,what is simple mail transfer protocol,smtp kali linux,hacking tutorial,cyber security coursekali linux,how to hack,hacking,kali linux tutorial,how to install kali linux,kali linux install,how to exploit open ports using metasploit,port 25 smtp exploit,exim smtp,exploit smtp,postal email server,about smtp,how to enumarate port25,how to exploit port 25,simple mail transfer protocol (smtp),simple mail transfer protocol,simple mail transfer protocol in hindi,smtp kali linux,hacking tutorial,cyber security course,metasploitable 2 hacking tutorial,metasploitable2 tutorial
#cybersecurity
#ethicalhacking
#webserver
#exploiting
Thanks For Watching……
————————————————————————————————————————–
social media
Facebook page: https://bit.ly/3VYIFIm
Instagram: https://bit.ly/3h83Zw7
Business email: jokerexe73@gmail.com
by Joker exe
linux smtp server


Tutorial how to make open ports? So i can Train my self and attack that device