How To Use The Windows Event Viewer For Cyber Security Audit
How do you view system event logs on a Windows operating system?
Start learning Cybersecurity today! ➡️ https://www.cybertrainingpro.com/
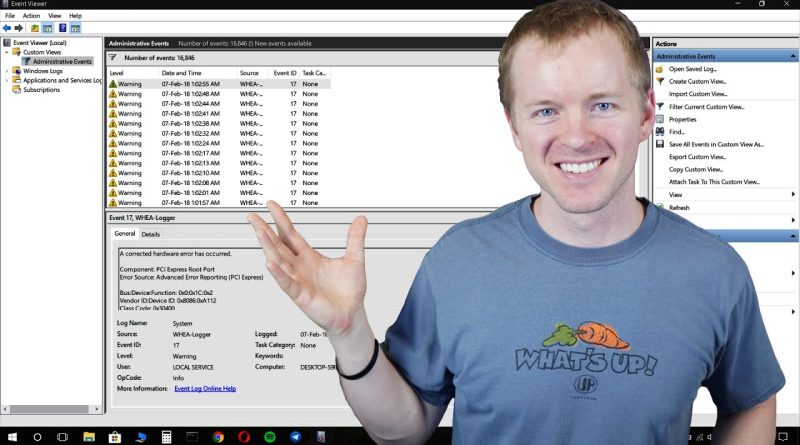
In technology jobs, there is an overwhelming pressure to aggregate event logs for all systems in a single location. What happens when we have a security incident or need to troubleshoot an individual system that might not be connected to the network? With the Windows Event Viewer, we can view the local events even if the system is isolated. I am not saying that you will need to do this frequently in most environments, but there will be times in your career where you need this skill.
In this video, I am going to walk you through using the Windows Event Viewer so that you can analyze an individual system’s event logs. I will also show you how to filter specific events by ID, by log, and by application for additional flexibility. Do not let this simple task hold you back in your career!
Learn About Microsoft Server: https://amzn.to/3ehKBpr
Windows PowerShell Cookbook: https://amzn.to/3fZldp5
Learn Windows PowerShell in a Month of Lunches: https://amzn.to/3i7TqoC
Learn PowerShell Scripting in a Month of Lunches: https://amzn.to/2Z6tfps
Blog Post: https://www.jongood.com/how-to-use-the-windows-event-viewer-for-cyber-security/
Make sure to watch the rest of the series on Windows Training For Cyber Security to better prepare you for joining the industry! https://www.youtube.com/playlist?list=PLErQ2qAXz3rpmfviDrlgkXogZ7sPhFtha
=============================
Today’s Video Sponsor
=============================
Are you interested in sponsoring content? ➡️ https://jongood.com/sponsor
=============================
Popular Cybersecurity Resources
=============================
Getting Started Resources & Free eBook ➡️ https://www.jongood.com/getstarted/
Cybersecurity Q&A ➡️ https://www.youtube.com/playlist?list=PLErQ2qAXz3roS8ubIclSRWwUHUy-jpj2r
Cybersecurity Projects ➡️ https://www.youtube.com/playlist?list=PLErQ2qAXz3rom8gtJNzm8iu_AAKNcXkFq
Cybersecurity Training & Career Services ➡️ https://www.CyberTrainingPro.com/
=============================
Cool Tech that I Use in My Studio
=============================
Gear List ➡️ http://jongood.com/affiliates/amazon/
=============================
Connect with me!
=============================
LinkedIn: ➡︎ https://www.linkedin.com/in/jongoodcyber/
Twitter: ➡︎ https://www.twitter.com/JonGoodCyber
Instagram: ➡︎ https://www.instagram.com/jongoodcyber/
⏰ Timecodes ⏰
0:00 How To Use The Windows Event Viewer For Cyber Security Audit
2:13 Opening the Windows Event Viewer
3:20 Alternate way to open the Windows Event Viewer
4:01 Filter Event Logs
5:15 Custom Views For Event Logs
7:05 Question of the Day (QOTD)
=============================
#WindowsEventViewer #WindowsBasics #WindowsSecurity
DISCLAIMER: I am an ambassador or affiliate for many brands referenced on the channel. As an Amazon Associate, I earn a commission from qualifying purchases.
DISCLAIMER (MUSIC): I only use royalty-free music and sound effects.
windows server



Resources to Learn Windows:
-Learn About Microsoft Server: https://amzn.to/3ehKBpr
-Windows PowerShell Cookbook: https://amzn.to/3fZldp5
-Learn Windows PowerShell in a Month of Lunches: https://amzn.to/3i7TqoC
-Learn PowerShell Scripting in a Month of Lunches: https://amzn.to/2Z6tfps
Hi,
Kindly be of help, how do I perform log analysis on Windows OS and Windows server
Everyone clicking on this video because someone touched something they weren't supposed to
you missed the easiest way to open event manager. just open server manager then go to the tools in the top most section and look for event viewer. Thats it.
Windows tutorials without indian, a bit confusing for me ;]
How can I remove specific events from the event log?
Very informative, thanks for sharing #Jon Good. From Bangladesh
my guy
Why does security SPP will occur in windows 10 & why does it completely shuts down all the applications in my system at that moment
Very informative, thanks for sharing Jon.
I 💜 this videooo…
Can you also see who deleted files???
Hi Is there any way to know what files are being copied from my laptop to a USB drive. It's timestamp and what folder or file copied… OR If copy log present in the system.
Hope its still relevant,i have a question to disable real time protection and find the event id(sounds simple) but when i do that the event id doesnot appear.. even when im in the local(configuration) any suggestions?
Hi John great video,after 3 years need t know somebody all of these stuff ?
Q: I got a Kaspersky file on windows log and I cam get rid of it to install a different antivirus.
Can we get the Event Log of a computer remotely ?
Hi Jon, thank you for the video :)!
I have a question about this. The event ID 4698 and the events of schtasks i can't see them, ¿why is it not displayed in the event viewer?
Thank you!
brief and precise, i didint know how to use event viewer until i saw this video
Thank you Jon. That was Good!
Hey Jon, I suspected someone was on my PC uninvited. I went to look at my event viewer logs and they have been cleared! I did not do this, could you help me out? Trying to figure out when they where cleared and when someone was on my PC, gods knows whats been installed. Can anyone help?
Can you tell us how can we convert the time format to UTC, for example, when we find a event Id and we have to write it in the forensic report it's very common to write the date and time in UTC format.
Hello Jon, i noticed that the event viewer no longer displays the username. how can we get the username for the event logon and logoff?
Also bears mentioning that you can add MMC snap-ins to view logs on remote computers in a domain. Super convenient as an admin
Thanks! Gotta investigate a laptop tomorrow
Thank you for this post. Some times if feels better to jump in as you just did but for trying Splunk or DeepBlueCLi
Explain the concept of logging? where are they located in windows and linux? sho b w an example of failed login logging in windows event viewer
Hi my friend. I am trying write script for task scheduler for sending realtime all logs to telegram channel. can you help me?
Hey jon,
Sorry i am learning about this but you are my best shot at getting the proof here. Long story short, some of the veryyy imp files have been deleted from google drive and even from trash. I know who did it from my laptop when i was away, it does say I deleted it because laptop had g-drive logged in. I am in reallll trouble now. All i want is a proof that my laptop was used between X-Y dates so that i can prove my innocence. I already am down the rabbit hole and i have reached here. Please guide me if this can be done from event viewer. All i want is confirmation that laptop was used during the dates when i wasn’t around. Even better if we can see someone opened g-drive.
Sorry but this video is a joke
I have a question and went to event viewer and few month ago I downloaded this application called solidworks. I deleted the application for solidworks but in the event viewer there is still a log file for SW any help? I just want to delete that log file. It’s under application and services 😭 I hate downloading school stuff on my personal gaming PC. I don’t want to clear the log I want to delete that log file***
Nice video bro i am also an IT guy
Thanks Jon Good
Sorry Jon, I like the way you present your videos I just assumed what you would be sharing would be more focused on what logs we would need to be investigating. For instance, the Firewall Log, the DNS log, obviously the Security log etc. Other than that, you present well, are clear and concise and can't fault you!
Hello. Do you have a reference you would recommend for looking up event ID’s? Thanks
Onboard system software is dece enough
0% audio. I tried other videos and they worked.
Thank You very much for this grate information…!!! In my computer shows to many times the ID 4672 Special Logon and ID 4624 Logon and I don´t know if this means tha some from out side is looking my personal information or it is just a simple thing from Windows Event…!!! Will you be so nice just to let me know if this could be dangerous or not…!!! I will appreciate so mucho…!!! I send you a big hug from México City…!!! God Bless You Always…!!!
Thanks for this very interesting vidéo.
how can you do this using Autopsy?
Wow. You’re Good
How can I filter logs by date(s)?
how to display those security events using c or c++ program
I have come across some events that occurred during the wee hours of the morning while I was sleeping. Is there a way for me to find out its location?