You ever seen these devices? Networking for Hackers and Cybersecurity professionals.
How long did it take you to see something new or learn something new in this video? If you want to be an Ethical Hacker or Cybersecurity Professional, you need to understand networking.
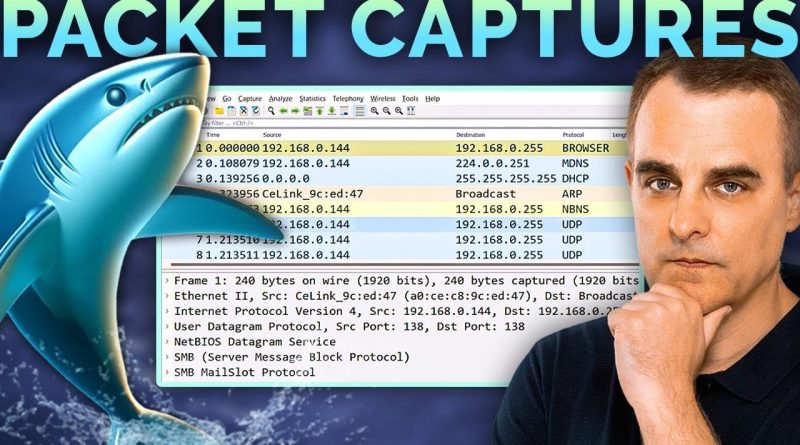
In this video I show you how to capture traffic using Wireshark and Ethereal using different scenarios:
1) Bus topology
2) Hub topology
3) Bridge topology
4) Switched topology
5) Port mirror / port span
6) Network Tap
7) VLANs
and more 🙂
// David’s SOCIAL //
Discord: https://discord.com/invite/usKSyzb
X: https://www.twitter.com/davidbombal
Instagram: https://www.instagram.com/davidbombal
LinkedIn: https://www.linkedin.com/in/davidbombal
Facebook: https://www.facebook.com/davidbombal.co
TikTok: http://tiktok.com/@davidbombal
YouTube: https://www.youtube.com/@davidbombal
// MY STUFF //
https://www.amazon.com/shop/davidbombal
// SPONSORS //
Interested in sponsoring my videos? Reach out to my team here: sponsors@davidbombal.com
/ MENU //
0:00 – Understand how networks work
0:50 – How to capture traffic on a bus network topology // Bus network explained
5:24 – Physical bus network demo // Remotely controlling two PCs
8:07 – Capturing traffic on a bus network demo // Ethereal demo
12:40 – Ethernet hub explained
13:15 – How to capture traffic on a star network topology // Star network topology explained
15:43 – Capturing traffic on a star network demo // Wireshark demo
17:16 – Collision domains explained
19:06 – Replacing ethernet hub with ethernet bridge // Physical ethernet bridge topology explained
20:06 – Capturing traffic on a bridge topology demo // Wireshark demo
21:19 – Ethernet bridge explained
24:01 – Replacing ethernet bridge with ethernet switch -// Physical ethernet switch topology explained
25:30 – Capturing traffic on a switch topology demo // Wireshark demo
27:23 – Ethernet switch explained
29:41 – Capturing traffic on a switch topology demo continued
32:14 – Port mirroring / spanning explanation demo
33:06 – Capturing traffic with an ethernet tap demo
35:00 – Routers explained
kali linux
linux
http
apache
tap
network tap
vlan
bridge
switch
router
nmap
ssl
http
https
ssh
telnet
chargen
port
port numbers
wireshark
bus
star
Please note that links listed may be affiliate links and provide me with a small percentage/kickback should you use them to purchase any of the items listed or recommended. Thank you for supporting me and this channel!
Disclaimer: This video is for educational purposes only.
#kalilinux #wireshark #hacker
by David Bombal
linux web server


How long did it take you to see something new or learn something new in this video? If you want to be an Ethical Hacker or Cybersecurity Professional, you need to understand networking.
In this video I show you how to capture traffic using Wireshark and Ethereal using different scenarios:
1) Bus topology
2) Hub topology
3) Bridge topology
4) Switched topology
5) Port mirror / port span
6) Network Tap
7) VLANs
and more 🙂
// David's SOCIAL //
Discord: https://discord.com/invite/usKSyzb
X: https://www.twitter.com/davidbombal
Instagram: https://www.instagram.com/davidbombal
LinkedIn: https://www.linkedin.com/in/davidbombal
Facebook: https://www.facebook.com/davidbombal.co
TikTok: http://tiktok.com/@davidbombal
YouTube: https://www.youtube.com/@davidbombal
// MY STUFF //
https://www.amazon.com/shop/davidbombal
// SPONSORS //
Interested in sponsoring my videos? Reach out to my team here: sponsors@davidbombal.com
/ MENU //
0:00 – Understand how networks work
0:50 – How to capture traffic on a bus network topology // Bus network explained
5:24 – Physical bus network demo // Remotely controlling two PCs
8:07 – Capturing traffic on a bus network demo // Ethereal demo
12:40 – Ethernet hub explained
13:15 – How to capture traffic on a star network topology // Star network topology explained
15:43 – Capturing traffic on a star network demo // Wireshark demo
17:16 – Collision domains explained
19:06 – Replacing ethernet hub with ethernet bridge // Physical ethernet bridge topology explained
20:06 – Capturing traffic on a bridge topology demo // Wireshark demo
21:19 – Ethernet bridge explained
24:01 – Replacing ethernet bridge with ethernet switch -// Physical ethernet switch topology explained
25:30 – Capturing traffic on a switch topology demo // Wireshark demo
27:23 – Ethernet switch explained
29:41 – Capturing traffic on a switch topology demo continued
32:14 – Port mirroring / spanning explanation demo
33:06 – Capturing traffic with an ethernet tap demo
35:00 – Routers explained
kali linux
linux
http
apache
tap
network tap
vlan
bridge
switch
router
nmap
ssl
http
https
ssh
telnet
chargen
port
port numbers
wireshark
bus
star
Please note that links listed may be affiliate links and provide me with a small percentage/kickback should you use them to purchase any of the items listed or recommended. Thank you for supporting me and this channel!
Disclaimer: This video is for educational purposes only.
#kalilinux #wireshark #hacker
So with the bus topology and the star topology, all machines or hosts receive the signals. Is it because they're broadcasting? 14:13
i tried to limit myself. but the traffic on the bus topology needs the terminators to kill the signal. havent learned that yet 8:46
2:50 the other drop cable with the tranceiver. imma stop posting for a moment. u were the frst YT IT guy i followed. so ofc ur content is useful to ME lol
2:28 vampire tap
2:22 10base5 cable. ive learned about these topologies and terms. seen a cpl cat5e where i work. im excited to learn
timestamp 1:45 ethernet tap
lol oh david. im new to all this! currently training for my net+…but timestamp 00:56 ethernet bridge
Cool! I've always wanted to see a bridge so thank you. I now have a better understanding of networking
Things i learn from this video:
AUI to BNC Transceiver (and in general the AUI port)
Ethereal
A good example of how a network bridge looks like
That a Network tap is hidden from the switch
A very good refresh of the things i already know
I watch alot of your videos on both youtube and udemy and this video help me understand how many things i have already learn over the years and that a lot of it comes from your content, thanks David.
Good vid. Ive never seen physical bus.
This is one of the best video you ever posted David
Love from India
Good to know
Thank you Devid for your restless efforts that help a needy one's like me are getting out off problems and still following your educational videos since the day one Begin training under the staff you know and faced problems i claimed and looking for your professional solution help fix all problems.
Can I ask you something?
I am researching about 10BASE-T1S protocol and I have to figure out how to analyze this protocol. I learned some information about wireshark but I don't know exactly how can I observe the errors. So;
1-) First of all, I know that 10base-t1s is used on wireshark but I am not sure, can you verify this?
2-) If I can analyze the 10base-t1s protocol on wireshark, how do I know if the message has been transmitted or how to see the error if the message has not been transmitted?
Thank you,
all the best , dear
Mr. Bombal
This is one of the best videos you have ever made! The way that you utilize visualizations of the devices, helped me understand the total functionality of each device. Moreover, I am a visual learner and most individuals that are Youtubers in the epic hacking area do not utilize visualizations , as you Have done in this video with the exception of network chunk. as each device was explained, you utilized effects that lit up each device which added to the visualization learning technique that most people are looking for when they are seeking to learn on YouTube channels! Again, I have learned more watching your new techniques, and I have learned in six months of attempting to learn on other channels! Please continue the visualization techniques! Excellent job!
2024 yall. Anyone UDP hone? Global 127.0000000.1 ?
Brings back my nightmare of a CCIE lab practical whereby the test could of consist of the following: DECNET, AppleTalk, SNA, Token Ring, X.25, frame Relay, BRI, ISDN, and Ethernet to name a few.
Thank you !
I would wager if Windows (all versions) computers weren't on the other side of firewalls and routers, if there were no foreign built motherboards, routers, switches, transceivers or any Integrated Circuits, more than half of hacking wouldn't be possible.
I'm from Germany and we only learn American English at school—but for you, I learnt British English. In every minute of the video, I learned something new. Thank you! Love your Content
3m10
might be good to map it to the OSI layer
but still a good video explaining why different broadcast domain is needed and CSMA/CD is a legacy thing now since no one actually uses hub now and collision domain is also a thing of the past times since a switch separates collision domain with each port, which i think cisco still test it in CCNA.
haven't seen a small 10G inline tap just google that thing cost 900USD?! omg
usually those will use probably gigamon
don't know if there is a SFP+ or QSPF28 small tap.
What actually is ethical hacking? Is that like saying im a christian but not really?
I knew some of the information you talk about but you made it more clearly and I also learned some new things thank you David Bombai 🙂
All of it was new to me, but I think you went over a weak spot on my system that they been exploiting