Introduction to Packet Analysis – Part 9: Packet Analysis with Wireshark (Part 1)
Author: Jeremy Druin
Twitter: @webpwnized
Thank you for watching. Please help by up voting, subscribing or even support this channel at https://www.youtube.com/user/webpwnized
Description: From the ISSA-KY Network Packet Analysis Workshop, this video series introduces the basics of the OSI packet model, application packet model and common network protocols. Later videos will discuss specific protocols such as TCP, IP, UDP and HTTP. Packets will be captured into PCAPs which are analyzed with Wireshark and Network Miner.
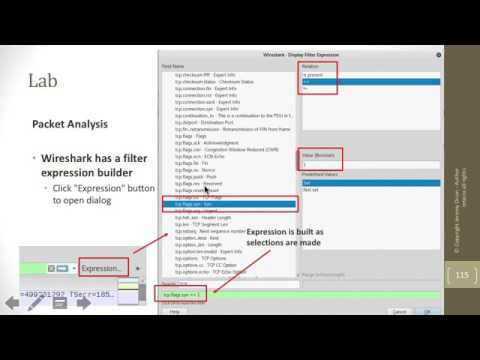
We continue the series on network packet analysis by analyzing network packets in PCAP files with Wireshark. Wireshark is available on most versions of Linux and is preinstalled on Kali Linux. It can be installed on Windows including Window 10. It is easy to use even for beginners and works with any files in the PCAP format. The PCAP format is the standard network packet capture file format allowing the files to be opened in tools such as Wireshark and Network Miner.
In this video, Wireshark usage is discussed and packets captured with TCPDump are used as examples in the demo.
Tools discussed in other videos are Wireshark, Network Miner, Scapy, TCPDump and Traceroute for Linux. Later videos will cover usage of some of these tools. Also, other videos on this channel discuss tools like scapy. For videos that go into depth on these tools please see videos at playlist https://www.youtube.com/playlist?list=PLZOToVAK85MqkNyx8VKPT7h9ZlxkX2krG.
If you would like access to the full course including the lab exercises and walk-through, please consider taking the course at http://ellipsisinfosec.teachable.com/p/introduction-to-network-packet-analysis-and-forensics
The webpwnized YouTube channel is dedicated to information security, security testing and ethical hacking. There is an emphasis on web application security but many other topics are covers. Some of these include forensics, network security, security testing tools and security testing processes. The channel provides videos to encourage software developers and system administrators to perform security testing. Also, the channel educates the next generation of security testers and bug bounty hunters who want to respectfully, legally and ethically help system owners that allow security testing.
by webpwnized
linux smtp client